Welcome back, my novice hackers!
As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.
One of the cardinal rules of hacking is: "If I can get physical access to the computer... GAME OVER!" This means that if I were given even just a few moments to the machine itself, I can hack anything I want from that computer—including Facebook passwords.
Aslo Read :- how to recover deleted data from android
I recognize that not all of you are technically savvy, though, that doesn't mean you can't be with some hard work. So this Facebook hack is for those of you without either the technical savvy or the work ethic to become so. All you need is a moment or two of unfettered physical access to the target's computer and you can easily have their Facebook password.
Remember Me?
This hack relies upon the fact that most of us want websites to remember us when we return. We don't want to put in our username and password every time we want to access the site, so we tell the browser to "Remember me." In that way, we don't need to re-authenticate and provide our password, our system simply remembers it and provides it to the website.
Of course, those passwords must be stored somewhere on our computer. The key is to know where those passwords are stored and how to crack the hashed passwords when we find them. For instance, Mozilla stores the users passwords at:
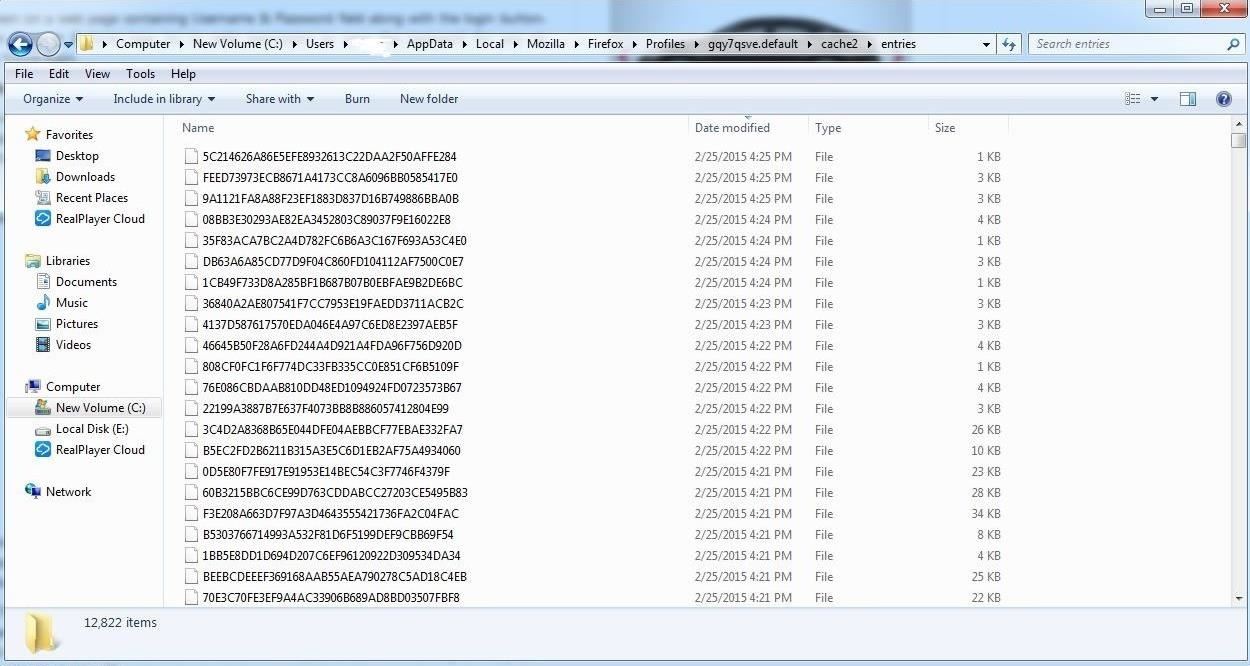
c:/Users/Username/AppData/Local/Mozilla/Firefox/Profiles/**.default/cache2/entries
As you can see in the screenshot below, I have displayed that directory and password hashes from a Windows 7 computer running Firefox 36. These are all the saved passwords from various websites that Firefox has stored.
Note that the location of these passwords is in different places for each browser and sometimes in different places on different operating systems with the same browser. Look for more on this subject in my Digital Forensics series in the near future.
Elcomsoft's Facebook Password Extraction Tool
Fortunately for us, there is a company in Russia named Elcomsoft.
This company employs first-rate cryptographers and they develop and sell software to crack various password encryption schemes. (As a side note, a cryptographer from Elcomsoft was the first person arrested and prosecuted under the DCMA when he came to the U.S. for a conference. He was eventually acquitted.)
Their software is listed as digital forensic tools, but they can just as easily be used for hacking purposes. One of their tools was used for the iCloud hack that revealed nude photos of Jennifer Lawrence and other Hollywood stars in August 2014.
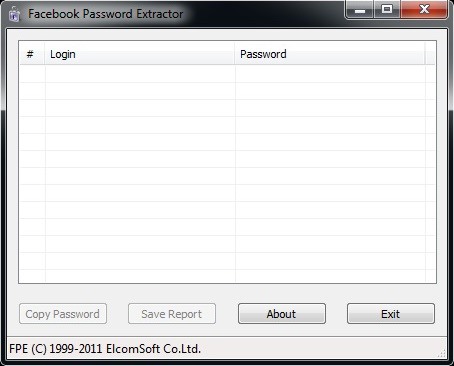
Elcomsoft developed a Windows tool named Facebook Password Extractor (FPE, for short) that extracts the user's Facebook password from its location on the user's system (the user must have used the "Remember me" feature) and then cracks it. Of course, we need physical access to the system to do this in most cases. Alternatively, if we can hack their system, we could upload this tool to the target system and then use it or we could simply download the user's browser password file and use this tool locally on our system.
You can download this free tool from Elcomsoft's website, which officially supports the following web browsers (though it may work on newer versions).
- Microsoft Internet Explorer (up to IE9)
- Mozilla Firefox (up to Firefox 4)
- Apple Safari (up to Safari 5)
- Opera (up to Opera 11)
- Google Chrome (up to Chrome 11)
The process of using this tool is almost idiot-proof. (Almost a requirement for Facebook hacking, wouldn't you agree?) You simply install it on the system whose Facebook password you want to extract and it does everything else.
One of the drawbacks to using this tool is that Elcomsoft released it back in 2011 and it has not been updated since. Maybe we should make this a Python project for the Null Byte community in the near future?
Look for more on Facebook hacking and developing the skills and arts of a professional hacker here in the near future, my novice hackers!